Brilliant Info About How To Prevent Data Misuse

Here a few tips about data backup that’ll help you do it effectively:
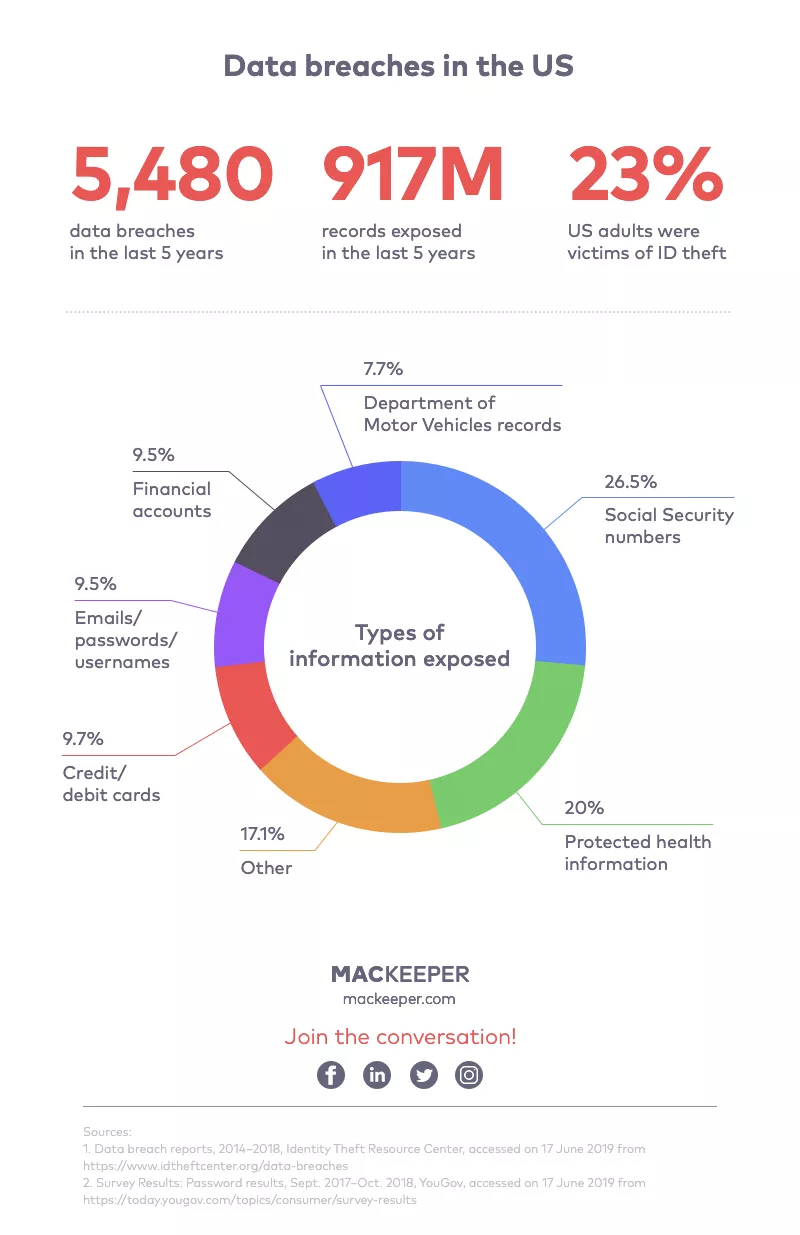
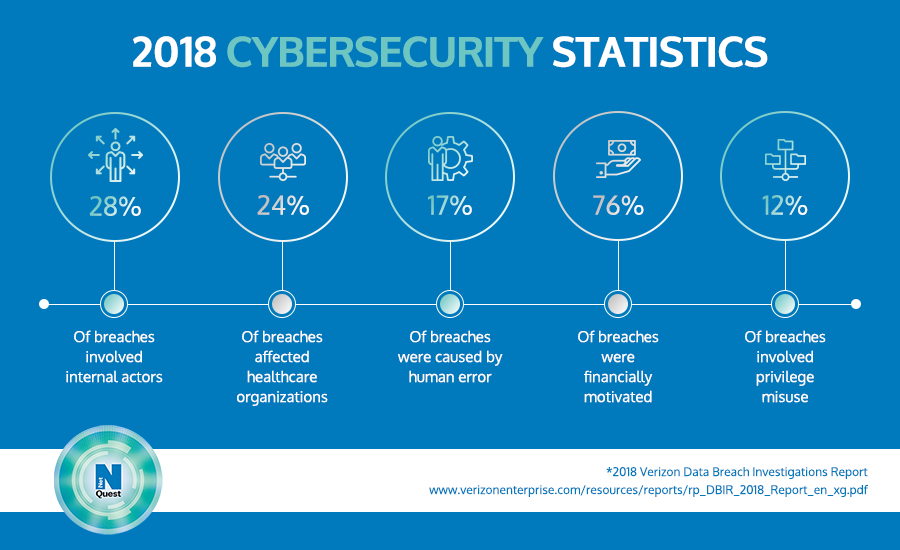
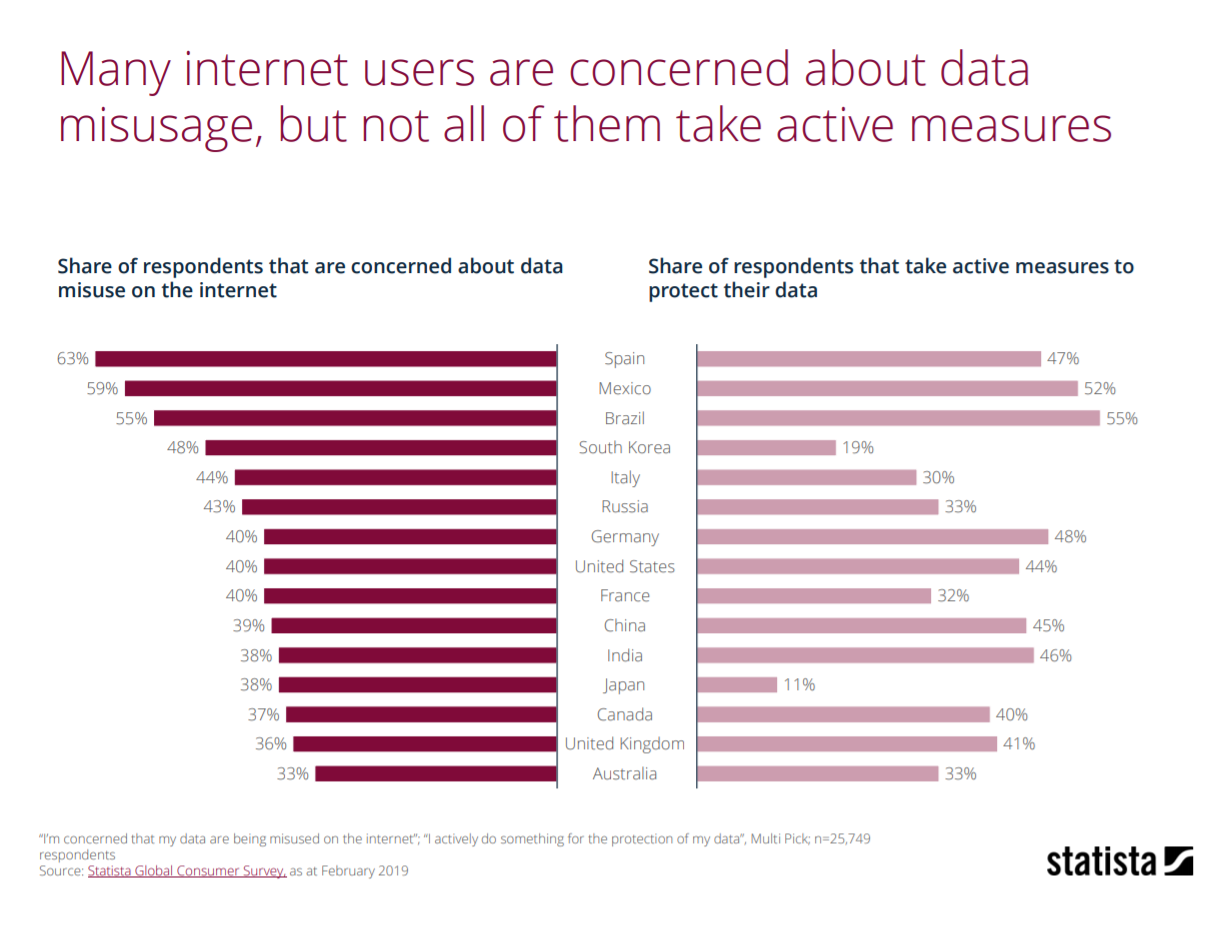
How to prevent data misuse. By not training your employees in the methods of cyber attackers or how to securely store and use sensitive information, you put them at risk of causing a data breach. Accessing computer material without permission, eg. Well, incidents of data misuse keep springing up like weeds.
One of the most popular ways to prevent unintentional data leakages is by using a vpn. The #1 most important preventative measure against data loss is to backup all of your data. You should be well aware of the data that your.
Implement identity and access management verifying the identity of each user that attempts. 6 steps to prevent misuse of data in your company 1. How to prevent computer misuse the data protection act.
Data leakages are also responsible for a high percentage of data misuse. This refers to the process in which raw data or plain text is scrambled into “ ciphertext ” so that it. Put protections in place to prevent data from being manipulated or misused.
Why this countermeasure matters allowing data within systems or prefilled forms to be manipulated by. This helps to provide protection against the. This was introduced to regulate personal data.
What is data misuse and how to prevent it? Keep at least one copy of your. One obvious place to start is the applications themselves.
![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/4-ways-figure1.jpg)
![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/4_ways/figure-1.jpg)
![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/4_ways/figure-2.jpg)
![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/4_ways/figure-3.jpg)
![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](http://www.ekransystem.com/sites/default/files/4_ways/open-4-Ways-to-Detect-and-Prevent-Misuse-of-Data.jpg)



![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/4_ways/figure-5.jpg)




![4 Ways To Detect And Prevent Data Misuse [With Examples] | Ekran System](https://www.ekransystem.com/sites/default/files/4_ways/figure-4.jpg)